Here's a great post over at the Malware Diaries about a recent phishing attempt involving an email reporting that you are due a tax refund:
Hotmail Spam Problems
If you've been receiving spam from a friend with a Hotmail account, or you own the Hotmail account that is sending out spam, please read the info below from Microsoft:
Recent reports of Account hijacks
This solution article provides information about the increase in reports that we have received about accounts been hijacked and spam mails been sent to customer's contact list without customer's knowledge.
Hotmail is seeing instances of accounts being "hijacked" by spammers who send emails out advertising an electronics website. The spam mails usually have subjects like "Good shopping good mood" and may go to your contact list in addition to a random list of emails. Indications that this is happening to you may include you being required to match the characters in the picture (to verify that you're a person and not an automated program) to send mails when you reach your limits.
Some of the other symptoms that our customers have noticed are:
- Deleted contacts
- Safe sender's list is deleted
- Deletion of Junk messages is set to "Immediately"
- Junk Mail Settings is set to "Exclusive"
The last symptom would prevent messages from being delivered to your Inbox. If you would like to change the Junk Mail Filter settings, visit this Solution Article for the steps.
Some of the other account setting that might be affected by this issue is your Signature.
To know how to delete the Signature that appears on your e-mail, follow these steps:
1. In the upper-right corner of the Windows Live Hotmail home page, click "Options" and then click "More options"
2. Under Customize your mail, click "Personal e-mail signature"
3. Delete the text or any image in the signature box, and then click "Save."
Note that you will still be able to login, and are in fact, "sharing" your account with the spammer.
Hotmail believes that this may be due to one of these reasons:
1. The user has fell victim to some type of phishing scheme - either they replied to an email threatening to close their account if they didn't provide their password, or they went to a website that looked like the Hotmail login page and provided their password.
If you have access to your account, we recommend that you change your password and secret question and answer immediately.
If you have lost access to your account, click here to regain access.
2. A virus on a computer that you have used to login to Hotmail at some point in the past.
If you login and see in your "sent items" folder mails that you haven't sent, or receive Non Delivery reports (NDRs) in your inbox, we recommend that you scan your computer for viruses and malware using a reliable Antivirus product (click here to go to Microsoft's anti-virus page). Once your computer has been cleaned, immediately change your current password to a "strong" password. Click here to know how to create a strong password.
The worm/virus sends various messages that entice users to click on a malicious link that leads to a Web site. Clicking on the said link downloads a copy of the worm onto message recipients' computers. Upon download, it then gathers e-mail addresses saved on the recipient's computer and sends itself out to all of those addresses.
There are a number of ways you can protect your computer against these viruses:
- Obtain the most recent virus definitions. You can visit your anti-virus company's website or call them to get more information.
- Be cautious about opening messages that contain links to websites.
- Be cautious when opening embedded links. Point your mouse cursor on the link and look at the underlying URL that displays in your browser status bar at the bottom and ensure that the URL makes sense for what the link states. Never login from one of these links. If a link directs you to login to a service that you use, instead go to that service by accessing the services website directly from your browser and not use the embedded link.
- Do not open attachments unless you are expecting them.
- Download the latest Microsoft updates frequently. To download the latest updates for Microsoft software, please visit the following links:
http://update.microsoft.com/windowsupdate/
http://office.microsoft.com/productupdates
If you feel that a virus has already infected your computer, you can get online support (or toll-free telephone support in the U.S. and Canada) for security-related issues such as viruses and security updates from the Microsoft Security Help and Support Team. Please click on the link below:
http://support.microsoft.com/default.aspx/gp/securityhome
For more information on how you can protect your computer, please click on the link below:
http://www.microsoft.com/security/default.mspx
In addition, to ensure the security of your Hotmail account, we highly recommend that you change your Hotmail password and Secret Question. To do this, please follow the steps below:
To change your Hotmail password, sign in to https://account.live.com and select the "Change" option next to Password. Or if you want a direct link, you can go directly to the Change Password Page.
To change your Secret Question, click here.
Please ensure that you have updated your passport profile information as much complete as possible including your alternate email address. The more complete and more recent this information is, the better chance we have of assisting you in the event your account gets compromised.
We want to assure you that your security and protection online is our top priority and we are dedicated to help you obtain support for security-related issues such as viruses and security updates.
Lady Gaga and Rhianna Lyrics sites exploit Java malware
It seems as though a vulnerability in Sun Java (which they say apparently isn't bad enough to patch out of band!) has already been exploited, whereby visitors to some lyrics sites will automatically be infected.
It appears as though Macs are not affected.
Please be aware and pass on to anybody who frequents these sites.
Here's a blog post by Roger Thompson of AVG
"Heads up - 0day ITW - Rihanna is a lure
Hi folks,
On April 9th, Tavis Ormandy published a proof of concept about how to use the latest version of Java to compromise a pc. You can read about it here. He notified Sun, but they weren't concerned enough to break their patch cycle, so he published the code.
The problem is that when Sun released Java 6, update 10 in April 2008, they introduced a new feature (it's not a bug, it's a feature folks) called Java Web Start. In order to make it easier for developers to install software, they created a method to execute a program from a website.
Duh
Now, hindsight is always 20-20, but it doesn't take a massive gift of insight to imagine the Bad Guys thinking that was a good idea for them too.
Because they designed it as a feature, it works, of course, with both IE and Firefox.
The code involved is really simple, and that makes it easy to copy, so it's not surprising that just five days later, we're detecting that code at an attack server in Russia.
The main lure so far seems to be a song lyrics publishing site, with Rihanna, Usher, Lady Gaga and Miley Cyrus being used, among others. Who'd have thought that Miley could be dangerous??? As soon as we figure out what's wrong with the lyrics site, we'll let them know so they can fix it.
Of course, this'll soon likely be everywhere, so Sun will need to issue an out of band patch.
In the mean time, to stay safe, you can either follow the mitigation strategies outlined by Tavis, or install LinkScanner.
So far, it's not in any of the exploit kits, as far as we can see, but it's a given that it soon will be. Tick.. tick.. tick..."
And a page about it a SC Magazine.
Mac OSX Security Update Available
Apple have a released security update 2010-003 which is recommended for all users and improves the security of Mac OS X.
Please go to Software Updates to download
Adobe Update Available
Adobe has released security updates to address multiple
vulnerabilities that affect the following:
* Adobe Reader 9.3.1 and earlier
* Adobe Acrobat 9.3.1 and earlier
* Adobe Reader 8.2.1 and earlier
* Adobe Acrobat 8.2.1 and earlier
These vulnerabilities may allow an attacker to execute arbitrary code
or cause a denial-of-service condition.
Please visit Adobe to download and update your product
Critical vulnerabilities have been identified in Adobe Reader 9.3.1 (and earlier versions) for Windows, Macintosh, and UNIX, Adobe Acrobat 9.3.1 (and earlier versions) for Windows and Macintosh, and Adobe Reader 8.2.1 (and earlier versions) and Adobe Acrobat 8.2.1 (and earlier versions) for Windows and Macintosh. These vulnerabilities could cause the application to crash and could potentially allow an attacker to take control of the affected system.
Adobe recommends users of Adobe Reader 9.3.1 and earlier versions for Windows, Macintosh and UNIX update to Adobe Reader 9.3.2. (For Adobe Reader users on Windows and Macintosh, who cannot update to Adobe Reader 9.3.2, Adobe has provided the Adobe Reader 8.2.2 update.) Adobe recommends users of Adobe Acrobat 9.3.1 and earlier versions for Windows and Macintosh update to Adobe Acrobat 9.3.2. Adobe recommends users of Acrobat 8.2.1 and earlier versions for Windows and Macintosh update to Acrobat 8.2.2.
Affected software versions
Adobe Reader 9.3.1 and earlier versions for Windows, Macintosh, and UNIX
Adobe Acrobat 9.3.1 and earlier versions for Windows and Macintosh
Solution
Adobe Reader
Users can utilize the product's automatic update feature. The default installation configuration runs automatic updates on a regular schedule and can be manually activated by choosing Help > Check for Updates.
Adobe Reader users on Windows can also find the appropriate update here:
http://www.adobe.com/support/downloads/product.jsp?product=10&platform=Windows.
Adobe Reader users on Macintosh can also find the appropriate update here:
http://www.adobe.com/support/downloads/product.jsp?product=10&platform=Macintosh.
Adobe Reader users on UNIX can find the appropriate update here:
ftp://ftp.adobe.com/pub/adobe/reader/unix/9.x/9.3.2/.
Adobe Acrobat
Users can utilize the product's automatic update feature. The default installation configuration runs automatic updates on a regular schedule and can be manually activated by choosing Help > Check for Updates.
Acrobat Standard and Pro users on Windows can also find the appropriate update here:
http://www.adobe.com/support/downloads/product.jsp?product=1&platform=Windows.
Acrobat Pro Extended users on Windows can also find the appropriate update here: http://www.adobe.com/support/downloads/product.jsp?product=158&platform=Windows.
Acrobat 3D users on Windows can also find the appropriate update here:
http://www.adobe.com/support/downloads/product.jsp?product=112&platform=Windows.
Acrobat Pro users on Macintosh can also find the appropriate update here:
http://www.adobe.com/support/downloads/product.jsp?product=1&platform=Macintosh.
Severity rating
Adobe categorizes these as critical updates and recommends that users apply the latest updates for their product installations.
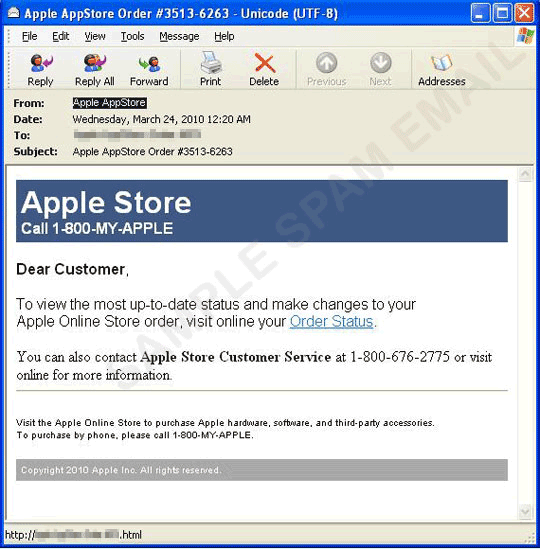
Apple Store Spam
This email seems to be gaining popularity, probably due to the recent iPad release.
Anybody that knows Apple or who has ever had an email relating to an Apple Store order will immediately know that it's bogus.
The design and layout is about as un-Apple is it possibly could be.
As ever, be wary of any such emails arriving in your inbox, especially if they include a number of CC addresses, and start with 'Dear Customer'
If the recipient follows the link inside the message, it will take him to a compromised webpage containing just a single linked word: "Visit". While he is wondering why the link didn't take him to the App Store, an exploit pack by the name "Eleonore" is being downloaded onto his machine. If he follows the "Visit" link in the hope of getting to the App Store page, he will be taken to a "Canadian Pharmacy" website.
The exploit pack drops a fake AV Trojan, and users should be extra careful because this particular file has only a 29% detection rate according to VirusTotal.
Worrying Wordpress Blog hacks
A large number of Worpdress users are finding their blog sites hacked by an injection of a web address into their databases.
The Networkads.net hack re-diredcts visitors to a site that tries to install malicious software.
There's a fix on the KrebsOnSecurity Blog
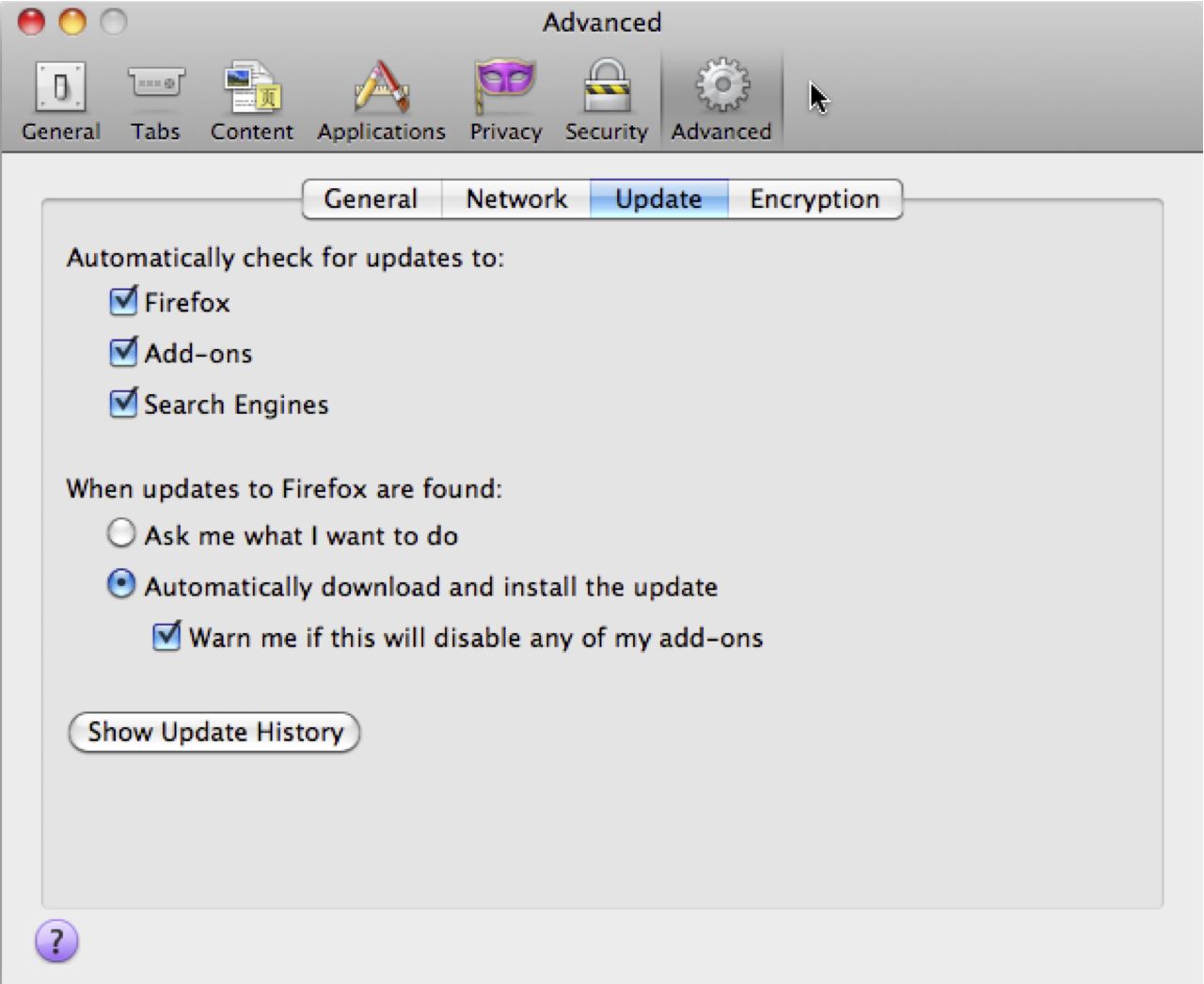
Firefox Update April 2nd
Just a reminder that Firefox was updated to 3.6.3.
Please update Firefox if you haven't already done so.
We suggest under Preferences, Advanced, Update to check all 3 automatic updates.
Adobe Reader Issues
There have been so many Adobe Acrobat & Reader vulnerabilities of late that we were considering making an Adobe page.
Put very simply, we (and Adobe) suggest making the following changes to your Reader and Acrobat preferences:
Go to Trust Management and uncheck "Allow opening of non-PDF file attachments with external applications"
Go to Javascript and uncheck "Enable Acrobat Javascript"
Further reading from the Adobe Blog
IRS Guide to the "Dirty Dozen" of US Tax Filing Scams
For anybody filing a US Tax Return online, read the following tips from the IRS:
Visa Warns of Rise In Keyloggers
Visa International has warned retailers that keylogging malware is on the rise hidden in card reading terminals.
The problem appears to be exacerbated due to the fact that most EPOS Tills are Windows-powered.
In an article at InfoSecurity, Mickey Boodaei says:
"Consumers, meanwhile, should also take precautions against keyloggers, says Boodaei, as criminals are increasingly targeting payment card information on the Internet.
Many malware variants, he explained, collect card data as customers type it in while making a purchase online. In addition, more sophisticated malware can also change payment pages on websites asking for additional card and personal information.
"Our research team have also come across malware variants that steal card information when you log onto your bank account. They frequently change the login page to request your card information and then send this information on to the criminals", he said.
According to Boodaei, the increasing sophistication of cybercriminals looking to rip-off retailers, as well as their card-carrying customers, is a problem that will not go away because, as existing avenues of card fraud are closed off, cybercriminals will attempt to open new ones up.
"Unfortunately, keyloggers are an ideal vehicle for card fraud, as they allow fraudsters to radiate trojans out via sophisticated bulk emailers and sit back for unwary recipients to click on the links and unwittingly install the keylogging malware on their Windows-driven machines", he said.
"Consumers can do their part by installing a browser add-in such as Trusteer's Rapport software, which is offered as a free download by banks such as HSBC, RBS/NatWest and the Santander Group. Retailers, meanwhile, should contact their till terminal supplier for advice on their own IT security options", he added.
Here is a link to Trusteers Rapport Browser plug-in and the download page
Apple Quicktime Exploit
There is a known (but already patched) vulnerability the affects the following versions of Apple OSX and Quicktime:
Apple QuickTime Player 7.6.5
Apple QuickTime Player 7.6.4
Apple QuickTime Player 7.6.2
Apple QuickTime Player 7.6.1
Apple QuickTime Player 7.6
Apple Mac OS X Server 10.6.2
Apple Mac OS X Server 10.6.1
Apple Mac OS X Server 10.6
Apple Mac OS X 10.6.2
Apple Mac OS X 10.6.1
Apple Mac OS X 10.6
BUT this has already all been patched in the latest Apple 10.6.3 update. Therefore, if you didn't update your Apple OS last week, please go ahead and do so without delay.
Products that are NOT vulnerable are:
Apple QuickTime Player 7.6.6
Apple Mac OS X Server 10.6.3
Apple Mac OS X 10.6.3
The news here is to always stay current with all software updates.
Whole Foods Facebook Scam
Whole Foods Market the American grocers is trying to clamp down on a series of Facebook-based scams that entice users with a purported $500 gift card.
The scam has been spreading virally through Facebook via "fan pages" with names like "Whole Foods Market Free $500 Gift Card Limited - first 12,000 fans only" and "Whole Foods FREE $500 Gift Card! Only Available for 36 hours!" The fan page asks Facebook users to add it as a fan, thus pushing awareness of the page through those users' Facebook networks, and then asks them to fill out a credit assessment and other forms that request personal information. The scam then uses a form of malware to crash users' computers and the information they have entered is left vulnerable.
The scams first emerged on Thursday, Whole Foods spokeswoman Libba Letton said, and though they have been working with Facebook to pull them down, new scams "keep popping up" as they're removed. "Throughout yesterday and this morning, we've been alerting them each time we see new ones, and we take them down," Letton told CNET. She said that if Whole Foods runs contests and gift card giveaways, they will only be orchestrated from the company's own Web site.
Whole Foods has also been using its Twitter account to reply to people who have tweeted about the scam or expressed concerns with it, providing answers like, "It's a scam, unaffiliated and unauthorized by us! Please help us report these pages so Facebook can shut them down." A warning announcement on its Facebook fan page is planned as well.
It's not yet clear who is operating the scams or whether any user information has been compromised.
"Groups and pages that attempt to trick people into taking a certain action or spamming their friends with invites violate our policies, and we have a large team of professional investigators who quickly remove these when we detect them or they're reported to us by our users," a Facebook representative told CNET. "We're working on ways to automate the flagging of these scam groups and pages so we can take action on them even more quickly."
The company recommends that users follow the Facebook Security fan page and report suspected scams when they see them.
(from CNET)
Microsoft Patch Tuesday
MICROSOFT PATCH DISCLOSURE - MARCH 30, 2010 UPDATE FROM EEYE
OVERVIEW
This month, Microsoft released an out-of-band patch which repairs a total of ten vulnerabilities. This patch addresses eight remote code execution vulnerabilities and two information disclosure vulnerabilities within Internet Explorer.
Both eEye's Blink® Professional and Blink® Personal Endpoint Security solutions protect from memory-corruption vulnerabilities generically without the need for any updates.
PATCH PRECEDENCE
Administrators are advised to apply this patch to affected systems immediately due to the common installation base of Internet Explorer 5.01 SP4, Internet Explorer 6, Internet Explorer 7, and Internet Explorer 8 on all Microsoft Windows operating systems.
As always, eEye suggests that users roll out Microsoft patches as fast as possible, preferably after testing the impact on internal applications and network continuity. For those who would like further information regarding the potential risks and remediation requirements of the patches announced today, please consider attending tomorrow's Vulnerability Expert Forumhosted by the eEye Security Research Team.
For more information on patch precedence, see the eEye Versa Newsletter article Patch Tuesday Prioritization for a Large Enterprise.
BULLETIN/ADVISORY SUMMARY
CRITICAL
MS10-018 - Cumulative Security Update for Internet Explorer (980182)
BULLETIN/ADVISORY DETAILS
Cumulative Security Update for Internet Explorer (980182)
http://www.microsoft.com/technet/security/Bulletin/MS10-018.mspx
Microsoft Severity Rating: Critical
eEye Severity Rating: Critical
Description
This security update resolves nine privately reported vulnerabilities and one publicly disclosed vulnerability in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
The security update addresses these vulnerabilities by modifying the way that Internet Explorer verifies the origin of scripts and handles objects in memory, content using encoding strings, and long URL.
- Uninitialized Memory Corruption Vulnerability - CVE-2010-0267
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has not been correctly initialized or has been deleted. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - Post Encoding Information Disclosure Vulnerability - CVE-2010-0488
An information disclosure vulnerability exists in the way that Internet Explorer handles content using specific encoding strings when submitting data. An attacker could exploit the vulnerability by constructing a specially crafted Web page that could allow information disclosure if a user viewed the Web page. An attacker who successfully exploited this vulnerability could view content from the local computer or another browser window in another domain or Internet Explorer zone. - Race Condition Memory Corruption Vulnerability - CVE-2010-0489
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that may have been corrupted due to a race condition. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - Uninitialized Memory Corruption Vulnerability - CVE-2010-0490
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has not been correctly initialized or has been deleted. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - HTML Object Memory Corruption Vulnerability - CVE-2010-0491
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has not been correctly initialized or has been deleted. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - HTML Object Memory Corruption Vulnerability - CVE-2010-0492
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has not been correctly initialized or has been deleted. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - HTML Element Cross-Domain Vulnerability - CVE-2010-0494
An information disclosure vulnerability exists in Internet Explorer that could allow script to gain access to a browser window in another domain or Internet Explorer zone. An attacker could exploit the vulnerability by constructing a specially crafted Web page that could allow information disclosure if a user viewed the Web page and then drags the browser window across a second browser window. - Memory Corruption Vulnerability - CVE-2010-0805
A remote code execution vulnerability exists in the way that Internet Explorer manages a long URL in certain situations. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - Uninitialized Memory Corruption Vulnerability - CVE-2010-0806
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has not been correctly initialized or has been deleted. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. - HTML Rendering Memory Corruption Vulnerability - CVE-2010-0807
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has been deleted. An attacker could exploit the vulnerability by constructing a specially crafted Web page. When a user views the Web page, the vulnerability could allow remote code execution. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Analysis
Attackers are likely to attempt to convince users to visit a specially crafted malicious web page, which would allow the attacker to gain control of the victim's system with the same rights as the currently logged on user. Attackers will primarily focus on developing exploits for Windows 2000, XP, 2003, Vista and 7 due to the remote code execution risks pertaining to these operating systems. Secondary targets will be Windows Server 2008 and Windows Server 2008 R2 since default Server Core Installations are not vulnerable to remote code execution, but other default installation types remain vulnerable to remote code execution. In a successful exploitation scenario, attackers are likely to install malicious backdoor programs which would be used to control compromised systems for launching attacks against other internal and/or external systems.
Recommendations
Administrators are urged to roll out this patch as soon as possible to all Windows systems. Until these systems are patched, it is strongly advised to disable ActiveX controls in Office 2007 products in order to mitigate Office documents being used to embed malicious web content.
Internet Explorer Vulnerability
Microsoft will be issuing a patch update on March 30th, so check for software updates on Tuesday.
How secure is your Mac?
Security expert Charlie Miller is due to disclose how he found 20 zero day Mac vulnerabilities at next weeks CanSecWest security conference.
Miller will stop short of exposing the actual vulnerabilities.
In a great analogy about PC security, Miller compared the Mac to a remote farmhouse without locks, suggesting that it's still a 'remote' enough platform to not be 'found' but is actually inherently insecure.
The days of safe Mac computing may well be numbered. We all expect the targeting to increase as the Mac's market share increases.
It's only a matter of time, but as long as you remain security conscious, the Mac is still currently the safest platform.
New Facebook email scam
There are reports of a new email scam pretending to be from Facebook, asking users to check their password enclosed in an attachment, because their password has 'been reset' due to a security flaw.
This plays on the current problem of accounts being hacked, meaning the recipients of such emails are more inclined to believe it.
Please alert all your friends on Facebook and help spread the word.
The scam email contains a zipped file that supposedly contains your new password.
What you're clicking on is actually a password stealer program that could steal not only the username and password of your Facebook account, but also details to other accounts such as online banking.
Please remember that Facebook would never send users such emails.
As ever, please be extremely wary of things arriving in your inbox asking you to open an attachment or click on a link.
Be even more suspicious if the grammar isn't right, which thankfully, it often isn't.
Spam loaded with malicious code
There have been recent reports of malicious code embedded in spam email messages impersonating the Department of Homeland Security.
The attacks arrive via unsolicited email messages that may contain subject lines related to DHS or other government activity.
These messages contain a link or attachment. If users click on this link or open the attachment, this will infect them with malicious code and the Zeus Trojan.
As ever:
- Do not click on links or attachments in email messages.
- Keep your antivirus software up to date
Safari Browser Update
Apple has just released a new security update for Safari, via its Software Update service.
This update is recommended for all Safari users and includes improvements to performance, stability, and security including:
- Performance improvements for Top Sites
- Stability improvements for 3rd-party plug-ins
- Stability improvements for websites with online forms and Scalable Vector Graphics
- Fixes an issue that prevented Safari from changing settings on some Linksys routers
- Fixes an issue that prevented some iWork.com users from commenting on documents
For detailed information on the security content of this update, please visit this site:http://support.apple.com/kb/HT1222.
Please update your Macs.
Microsoft Patch Tuesday
Microsoft fixed eight vulnerabilities in it's recent patch update but reports on a zero day vulnerability that exists in Internet Explorer.
We would advise updating Windows if you haven't already, and use the latest build of Firefox rather than IE