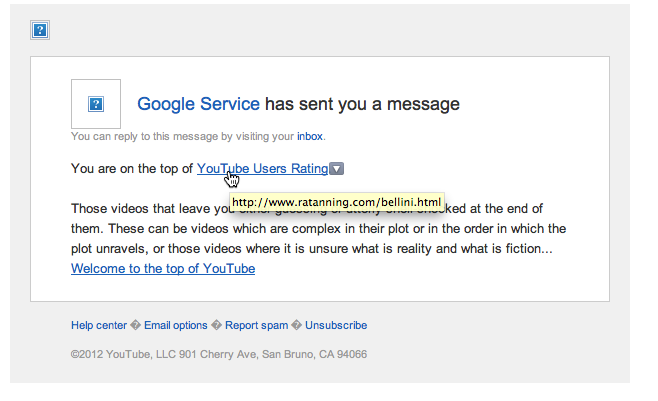
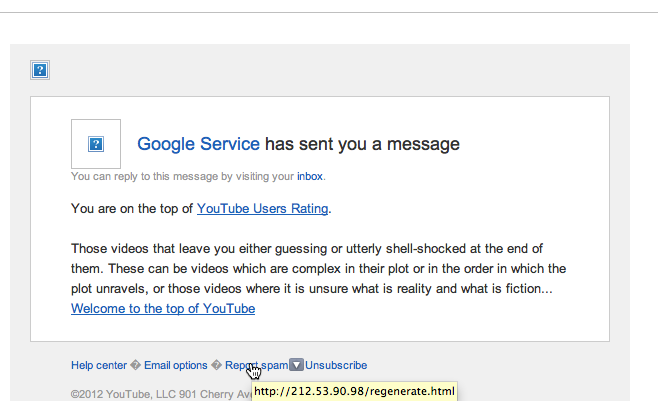
It seems like there's been a number of Twitter accounts hacked in the last few days.
If you've received a password reset request from Twitter via email, we urge you to change your password immediately, BUT, as ever, go direct to the website through your browser, rather than clicking a link in an email....just in case.
It's also worth reminding you of the importance of not using the same password for Twitter as you do for your online banking or any other sensitive website.
As in this case, if your password is stolen, it can potentially be used wherever else you log in, if you use the same password.
Even if you haven't had a recent password reset request, it might just be worth thinking about changing yours anyway. Think of it as a bit of house-keeping.
Also consider adding something to your password that is particular to that site, that you can easily remember, and that will make it different to your other passwords.
Don't delay - do it today!